Latest News
Showing 40 of 1000 articles
January 14, 2026

OpenAI's hidden ChatGPT Translate tool takes on Google Translate
OpenAI has quietly rolled out a new ChatGPT feature called ChatGPT Translate, and it looks very similar to Google Translate on the web.

South Korean giant Kyowon confirms data theft in ransomware attack
The Kyowon Group (Kyowon), a South Korean conglomerate, disclosed that a cyberattack has disrupted its operations and customer information may have been exposed in the incident.
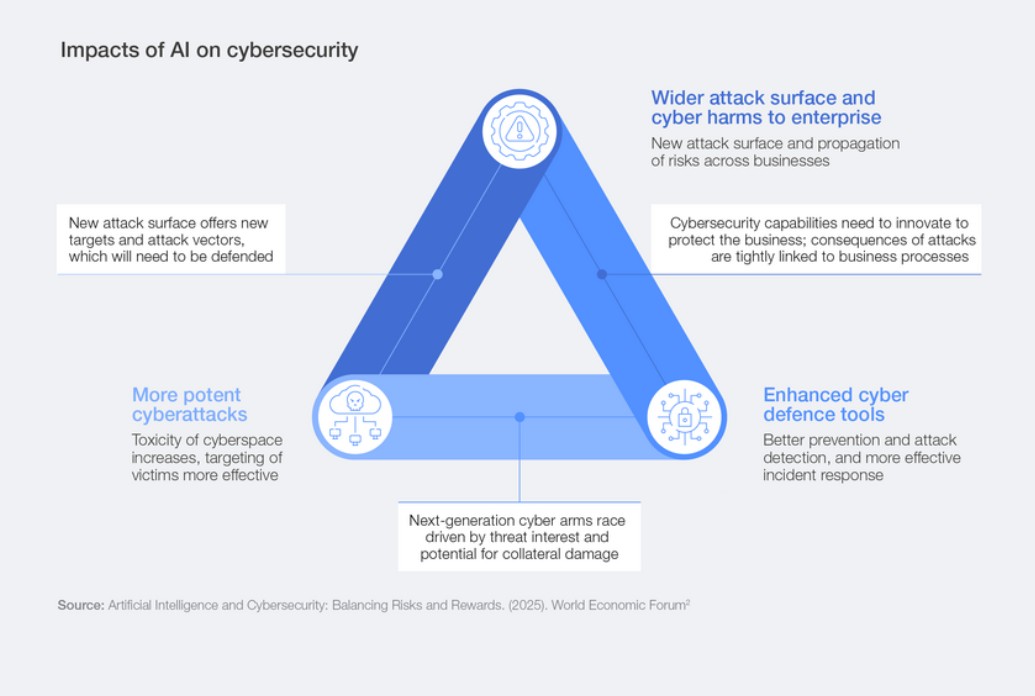
AI Security Is Top Cyber Concern: World Economic Forum
AI is expected to be “the most significant driver of change in cybersecurity” this year, according to the World Economic Forum’s annual cybersecurity outlook. That was the view of 94% of the more than 800 cybersecurity leaders surveyed by the organization for its Global Cybersecurity Outlook 2026 report published this week. The report, a collaboration with Accenture, also looked at other cybersecurity concerns such as geopolitical risk and preparedness, but AI security issues are what’s most on the minds of CEOs, CISOs and other top security leaders, according to the report. One interesting data point in the report is a divergence between CEOs and CISOs. Cyber-enabled fraud is now the top concern of CEOs, who have moved their focus from ransomware to “emerging risks such as cyber-enabled fraud and AI vulnerabilities.” CISOs, on the other hand, are more concerned about ransomware and supply chain resilience, more in line with the forum’s 2025 report. “This reflects how cybersecurity priorities diverge between the boardroom and the front line,” the report said. Top AI Security Concerns C-level leaders are also concerned about AI-related vulnerabilities, which were identified as the fastest-growing cyber risk by 87% of respondents (chart below). Cyber-enabled fraud and phishing, supply chain disruption, exploitation of software vulnerabilities and ransomware attacks were also cited as growing risks by more than half of survey respondents, while insider threats and denial of service (DoS) attacks were seen as growing concerns by about 30% of respondents. [caption id="attachment_108654" align="aligncenter" width="1041"] Growing cybersecurity risks (World Economic Forum)[/caption] The top generative AI (GenAI) concerns include data leaks exposing personal data, advancement of adversarial capabilities (phishing, malware development and deepfakes, for example), the technical security of the AI systems themselves, and increasingly complex security governance (chart below). [caption id="attachment_108655" align="aligncenter" width="1038"] GenAI security concerns[/caption] Concern About AI Security Leads to Action The increasing focus on AI security is leading to action within organizations, as the percentage of respondents assessing the security of AI tools grew from 37% in 2025 to 64% in 2026. That is helping to close “a significant gap between the widespread recognition of AI-driven risks and the rapid adoption of AI technologies without adequate safeguards,” the report said, as more organizations are introducing structured processes and governance models to more securely manage AI. About 40% of organizations conduct periodic reviews of their AI tools before deploying them, while 24% do a one-time assessment, and 36% report no assessment or no knowledge of one. The report called that “a clear sign of progress towards continuous assurance,” but noted that “roughly one-third still lack any process to validate AI security before deployment, leaving systemic exposures even as the race to adopt AI in cyber defences accelerates.” The forum report recommended protecting data used in the training and customization of AI models from breaches and unauthorized access, developing AI systems with security as a core principle, incorporating regular updates and patches, and deploying “robust authentication and encryption protocols to ensure the protection of customer interactions and data.” AI Adoption in Security Operations The report noted the impact of AI on defensive cybersecurity tools and operations. “AI is fundamentally transforming security operations – accelerating detection, triage and response while automating labour-intensive tasks such as log analysis and compliance reporting,” the report said. “AI’s ability to process vast datasets and identify patterns at speed positions it as a competitive advantage for organizations seeking to stay ahead of increasingly sophisticated cyberthreats.” The survey found that 77% of organizations have adopted AI for cybersecurity purposes, primarily to enhance phishing detection (52%), intrusion and anomaly response (46%), and user-behavior analytics (40%). Still, the report noted a need for greater knowledge and skills in deploying AI for cybersecurity, a need for human oversight, and uncertainty about risk as the biggest obstacles facing AI adoption in cybersecurity. “These findings indicate that trust is still a barrier to widespread AI adoption,” the report said. Human oversight remains an important part of security operations even among those organizations that have incorporated AI into their processes. “While AI excels at automating repetitive, high-volume tasks, its current limitations in contextual judgement and strategic decision-making remain clear,” the report said. “Over-reliance on ungoverned automation risks creating blind spots that adversaries may exploit.” Adoption of AI cybersecurity tools varies by industry, the report found. The energy sector prioritizes intrusion and anomaly detection, according to 69% of respondents who have implemented AI for cybersecurity. The materials and infrastructure sector emphasizes phishing protection (80%); and the manufacturing, supply chain and transportation sector is focused on automated security operations (59%). Geopolitical Cyber Threats Geopolitics was the top factor influencing overall cyber risk mitigation strategies, with 64% of organizations accounting for geopolitically motivated cyberattacks such as disruption of critical infrastructure or espionage. The report also noted that “confidence in national cyber preparedness continues to erode” in the face of geopolitical threats, with 31% of survey respondents “reporting low confidence in their nation’s ability to respond to major cyber incidents,” up from 26% in the 2025 report. Respondents from the Middle East and North Africa express confidence in their country’s ability to protect critical infrastructure (84%), while confidence is lower among respondents in Latin America and the Caribbean (13%). “Recent incidents affecting key infrastructure, such as airports and hydroelectric facilities, continue to call attention to these concerns,” the report said. “Despite its central role in safeguarding critical infrastructure, the public sector reports markedly lower confidence in national preparedness.” And 23% of public-sector organizations said they lack sufficient cyber-resilience capabilities, the report found.
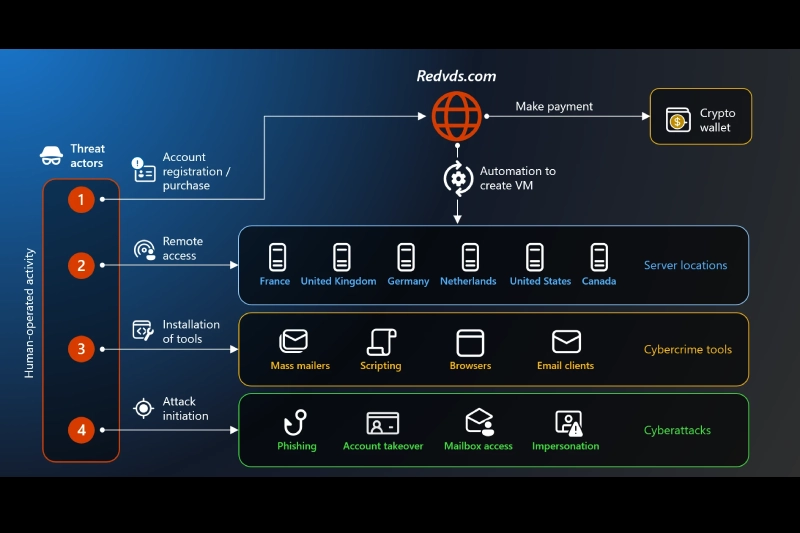
Microsoft Crushes Cybercrime Subscription Service Behind $40 Million Fraud Spree
A pharmaceutical company lost cancer treatment funding, a Florida condo association lost half a million dollars, and thousands more fell victim—all thanks to a $24-per-month criminal marketplace. Microsoft seized control of RedVDS, a global cybercrime subscription service that enabled fraud at industrial scale, marking the tech giant's 35th civil action against cybercrime infrastructure. The coordinated takedown, executed alongside law enforcement in the United States, United Kingdom, Germany and Europol, shut down a marketplace that powered millions in fraud losses with virtual computers available for less than the cost of a Netflix subscription. RedVDS operated like any legitimate software-as-a-service platform, complete with a customer dashboard, loyalty programs and referral bonuses. But instead of productivity tools, it sold disposable virtual machines running unlicensed Windows software that criminals used to launch attacks anonymously and at scale. "For as little as $24 a month, RedVDS provides criminals with access to disposable virtual computers that make fraud cheap, scalable, and difficult to trace," Steven Masada, assistant general counsel of Microsoft's Digital Crimes Unit, wrote in the company's announcement. The service fueled roughly $40 million in reported fraud losses in the United States alone since March 2025. But that figure represents only confirmed cases—the actual damage likely reaches far higher because fraud frequently goes unreported and victims span the globe. Among those hit hardest was H2-Pharma, an Alabama pharmaceutical company that lost more than $7.3 million earmarked for lifesaving cancer treatments, mental health medications and children's allergy drugs. The Gatehouse Dock Condominium Association in Florida lost nearly $500,000 in resident-contributed funds intended for essential repairs. Both organizations joined Microsoft as co-plaintiffs in the legal action. RedVDS Sent 1 Million Phishing Mails Daily The scale of RedVDS's operations reveals how cybercrime-as-a-service platforms have industrialized digital theft. In just one month, more than 2,600 distinct RedVDS virtual machines sent an average of one million phishing messages daily to Microsoft customers alone. While Microsoft's defenses blocked most attempts—part of the 600 million cyberattacks it stops every day—the sheer volume meant some still reached inboxes. Since September 2025, RedVDS-enabled attacks compromised or fraudulently accessed more than 191,000 organizations worldwide. These figures represent only Microsoft's visibility across its customer base, suggesting the true impact extends far beyond what any single company can measure. Criminals weaponized RedVDS primarily for business email compromise, a sophisticated fraud tactic where attackers infiltrate email accounts, monitor conversations and wait for the perfect moment to strike. When a payment or wire transfer approaches, they impersonate trusted parties and redirect funds, often moving money within seconds. [caption id="attachment_108648" align="aligncenter" width="600"] Source: Microsoft[/caption] Special Focus on Real Estate Domain, Among Others The service proved especially devastating in real estate transactions. Attackers compromised accounts belonging to realtors, escrow agents and title companies, then sent strategically timed emails with fraudulent payment instructions designed to divert closing funds and escrow payments. Microsoft observed RedVDS activity affecting more than 9,000 customers in the real estate sector, with particularly severe impacts in Canada and Australia. But the threat extended far beyond property deals. Construction companies, manufacturers, healthcare providers, logistics firms, educational institutions and legal services all fell victim to RedVDS-enabled scams that disrupted everything from production lines to patient care. What made RedVDS particularly dangerous was how criminals enhanced their attacks with artificial intelligence. Attackers paired the service with generative AI tools that identified high-value targets faster and generated realistic, multimedia email threads mimicking legitimate correspondence. In hundreds of cases, Microsoft observed criminals leveraging face-swapping, video manipulation and voice cloning AI to impersonate individuals with disturbing accuracy. The coordinated takedown seized two domains hosting RedVDS's marketplace and customer portal while laying groundwork to identify the individuals behind the operation. Germany's Public Prosecutor's Office Frankfurt am Main and the German State Criminal Police Office Brandenburg participated in the action, while Europol's European Cybercrime Centre worked to disrupt the broader network of servers and payment systems supporting RedVDS customers. Microsoft's action builds on the company's sustained strategy through its Digital Crimes Unit, which has now launched 35 civil actions targeting cybercrime infrastructure. The company also participates in global initiatives including the National Cyber-Forensics and Training Alliance and the Global Anti-Scam Alliance . With the RedVDS disruption, Microsoft has shown a shift in approach from chasing individual attackers to dismantling the services enabling crime at scale. As cybercrime-as-a-service platforms continue emerging, this infrastructure-focused strategy aims to make criminal operations harder to sustain and easier for potential victims to avoid. Masada stressed that falling victim to these schemes should carry no stigma, noting that organized, professional criminal groups execute attacks by intercepting and manipulating legitimate communications between trusted parties. Simple precautions can significantly reduce risk: questioning urgent requests, verifying payment instructions through known contact numbers, watching for subtle email address changes, enabling multifactor authentication, keeping software updated and reporting suspicious activity to law enforcement. Also read: Microsoft Disrupts Vanilla Tempest Campaign Using Fraudulent Code-Signing Certificates

France fines Free Mobile €42 million over 2024 data breach incident
The French data protection authority (CNIL) has imposed cumulative fines of €42 million on Free Mobile and its parent company, Free, for inadequate protection of customer data against cyber threats.

Researchers Null-Route Over 550 Kimwolf and Aisuru Botnet Command Servers
The Black Lotus Labs team at Lumen Technologies said it null-routed traffic to more than 550 command-and-control (C2) nodes associated with the AISURU/Kimwolf botnet since early October 2025. AISURU and its Android counterpart, Kimwolf, have emerged as some of the biggest botnets in recent times, capable of directing enslaved devices to participate in distributed denial-of-service (DDoS)

Exploit code public for critical FortiSIEM command injection flaw
Technical details and a public exploit have been published for a critical vulnerability affecting Fortinet's Security Information and Event Management (SIEM) solution that could be leveraged by a remote, unauthenticated attacker to execute commands or code.

Exploit code public for critical FortiSIEM command injection flaw
Technical details and a public exploit have been published for a critical vulnerability affecting Fortinet's Security Information and Event Management (SIEM) solution that could be leveraged by a remote, unauthenticated attacker to execute commands or code.

Verizon Wireless outage puts phones in SOS mode without cell service
Verizon Wireless is suffering a massive outage in the US, with customers reporting their phones stuck in SOS mode with no cellular service.

Monroe University suffers data breach impacting 320,000 people
Monroe University has disclosed a major data breach affecting more than 320,000 individuals, following a prolonged forensic investigation that concluded nearly a year after the intrusion took place. Although no evidence of fraud or identity theft has been detected, the exposed data includes a broad spectrum of sensitive personal information. The breach was first uncovered … The post Monroe University suffers data breach impacting 320,000 people appeared first on CyberInsider.
Investor Lawsuit Over CrowdStrike Outage Dismissed
A judge has ruled that the plaintiffs failed to demonstrate intent to defraud investors.

Microsoft updates Windows DLL that triggered security alerts
Microsoft has resolved a known issue that was causing security applications to incorrectly flag a core Windows component, the company said in a service alert posted this week.

AI surges among top business risk concerns, while cybersecurity holds firm
A report from Allianz Commercial shows the rapid embrace of AI is posing new challenges for enterprise leaders.

'VoidLink' Malware Poses Advanced Threat to Linux Systems
Researchers discovered a modular, "cloud-first" framework that is feature-rich and designed to maintain stealthy, long-term access to Linux environments.

Trump resubmits Sean Plankey’s CISA director nomination
It’s unclear when the Senate will act on Plankey’s nomination, which stalled last year after multiple senators blocked it.

AI security firm, depthfirst, announces $40 million series A
The company used an AI-native platform to help companies fight threats.

US cargo tech company publicly exposed its shipping systems and customer data to the web
Shipping tech company Bluspark left internal plaintext passwords, including those of executives, exposed to the internet, at a time when hacks in the shipping industry are on the rise.

AI Agents Are Becoming Privilege Escalation Paths
AI agents have quickly moved from experimental tools to core components of daily workflows across security, engineering, IT, and operations. What began as individual productivity aids, like personal code assistants, chatbots, and copilots, has evolved into shared, organization-wide agents embedded in critical processes. These agents can orchestrate workflows across multiple systems, for example:

RedVDS Cybercrime Service Disrupted by Microsoft and Law Enforcement
RedVDS enables threat actors to set up servers that can be used for phishing, BEC attacks, account takeover, and fraud.

France fines Free €42 million over 2024 data breach affecting 24M clients
France’s data protection authority, the CNIL, has imposed a combined €42 million fine on Free Mobile and its parent company Free SAS for failing to implement adequate security measures that led to a large-scale data breach in October 2024. The breach exposed sensitive customer data linked to 24 million subscribers. The penalties, €27 million for … The post France fines Free €42 million over 2024 data breach affecting 24M clients appeared first on CyberInsider.

Hackers Exploit c-ares DLL Side-Loading to Bypass Security and Deploy Malware
Security experts have disclosed details of an active malware campaign that's exploiting a DLL side-loading vulnerability in a legitimate binary associated with the open-source c-ares library to bypass security controls and deliver a wide range of commodity trojans and stealers. "Attackers achieve evasion by pairing a malicious libcares-2.dll with any signed version of the legitimate ahost.exe (

Predator Spyware Turns Failed Attacks Into Intelligence for Future Exploits
The Predator spyware is more sophisticated and dangerous than previously realized.
Reprompt attack let hackers hijack Microsoft Copilot sessions
Researchers identified an attack method dubbed "Reprompt" that could allow attackers to infiltrate a user's Microsoft Copilot session and issue commands to exfiltrate sensitive data.
Modern chips exposed to new “Memory Disorder” side-channel attack
A new powerful side-channel attack called MEMORY DISORDER is capable of leaking information from modern CPUs and GPUs from Intel, Apple, and AMD, without relying on timers. The implications of the research are far-reaching, demonstrating practical covert channels and application fingerprinting across multiple platforms, including AMD's Radeon GPUs. The technical paper explores how common microarchitectural … The post Modern chips exposed to new “Memory Disorder” side-channel attack appeared first on CyberInsider.

Novee Emerges From Stealth With $51.5 Million in Funding
Novee provides continuous AI-driven penetration testing to uncover and address novel vulnerabilities.

Firefox 147 tightens web security, reduces data sharing with Google
Mozilla has released Firefox 147 to the stable channel, introducing enhanced web security via Safe Browsing V5, improved video playback on AMD GPUs, native WebGPU support for Apple Silicon Macs, and patches for multiple high-impact vulnerabilities. Privacy and security upgrades A key highlight of this release is Firefox’s migration from Safe Browsing V4 to V5, … The post Firefox 147 tightens web security, reduces data sharing with Google appeared first on CyberInsider.

Cloud marketplace Pax8 accidentally exposes data on 1,800 MSP partners
Cloud marketplace and distributor Pax8 has confirmed that it mistakenly sent an email to fewer than 40 UK-based partners containing a spreadsheet with internal business information, including MSP customer and Microsoft licensing data.

Fortinet Fixes Critical FortiSIEM Flaw Allowing Unauthenticated Remote Code Execution
Fortinet has released updates to fix a critical security flaw impacting FortiSIEM that could allow an unauthenticated attacker to achieve code execution on susceptible instances. The operating system (OS) injection vulnerability, tracked as CVE-2025-64155, is rated 9.4 out of 10.0 on the CVSS scoring system. "An improper neutralization of special elements used in an OS command ('OS command

Victorian Department of Education says hackers stole students’ data
The Department of Education in Victoria, Australia, notified parents that attackers gained access to a database containing the personal information of current and former students.

New Research: 64% of 3rd-Party Applications Access Sensitive Data Without Justification
Research analyzing 4,700 leading websites reveals that 64% of third-party applications now access sensitive data without business justification, up from 51% in 2024. Government sector malicious activity spiked from 2% to 12.9%, while 1 in 7 Education sites show active compromise. Specific offenders: Google Tag Manager (8% of violations), Shopify (5%), Facebook Pixel (4%). Download the

Robo-Advisor Betterment Discloses Data Breach
A threat actor breached Betterment’s systems, accessed customer information, and sent scam crypto-related messages.

Fortinet Patches Critical Vulnerabilities in FortiFone, FortiSIEM
Exploitable without authentication, the two security defects could lead to configuration leak and code execution.

Microsoft: Windows 365 update blocks access to Cloud PC sessions
Microsoft confirmed that a recent Windows 365 update is blocking customers from accessing their Microsoft 365 Cloud PC sessions.

Chrome 144, Firefox 147 Patch High-Severity Vulnerabilities
The two browser updates resolve 26 security defects, including bugs that could be exploited for code execution.

Microsoft Fixes 114 Windows Flaws in January 2026 Patch, One Actively Exploited
Microsoft on Tuesday rolled out its first security update for 2026, addressing 114 security flaws, including one vulnerability that it said has been actively exploited in the wild. Of the 114 flaws, eight are rated Critical, and 106 are rated Important in severity. As many as 58 vulnerabilities have been classified as privilege escalation, followed by 22 information disclosure, 21 remote code

Monroe University says 2024 data breach affects 320,000 people
Monroe University revealed that threat actors stole the personal, financial, and health information of over 320,000 people after breaching its systems in a December 2024 cyberattack.

Critical Node.js Vulnerability Can Cause Server Crashes via async_hooks Stack Overflow
Node.js has released updates to fix what it described as a critical security issue impacting "virtually every production Node.js app" that, if successfully exploited, could trigger a denial-of-service (DoS) condition. "Node.js/V8 makes a best-effort attempt to recover from stack space exhaustion with a catchable error, which frameworks have come to rely on for service availability," Node.js's

MS-ISAC Flags High-Risk Security Flaws in Fortinet Products
A new cybersecurity advisory from the Multi-State Information Sharing and Analysis Center (MS-ISAC) is alerting organizations to multiple vulnerabilities affecting Fortinet products, some of which could allow attackers to execute arbitrary code on impacted systems. The advisory, identified as MS-ISAC Advisory 2026-003, was issued on January 13, 2026, and applies to a wide range of enterprise, government, and education-focused technologies. Among the affected solutions are FortiSandbox, FortiWeb, and FortiVoice, along with FortiOS, FortiClientEMS, FortiSwitchManager, FortiProxy, FortiFone, FortiSIEM, and FortiSASE. FortiOS, Fortinet’s proprietary operating system, is particularly notable because it is used across multiple product lines, meaning vulnerabilities within it can have cascading effects. FortiSandbox, which performs advanced threat detection by analyzing suspicious files and network traffic for zero-day malware and ransomware, is impacted by a server-side request forgery vulnerability. FortiWeb, a web application firewall designed to protect applications and APIs from attacks such as SQL injection and cross-site scripting, may also be indirectly affected through its reliance on FortiOS. FortiVoice, a unified communications platform that supports voice, chat, conferencing, and fax services, is impacted by a filesystem-related vulnerability that could allow file deletion under certain conditions. Technical Details of MS-ISAC Advisory MS-ISAC reports that the most severe vulnerabilities could allow arbitrary code execution within the context of affected service accounts. If those service accounts are configured with elevated privileges, an attacker could install programs, alter or delete data, or create new accounts with full user rights. Systems that enforce least-privilege access models may experience reduced impact. One of the most critical issues is a heap-based buffer overflow vulnerability (CWE-122) in the cw_acd daemon used by FortiOS and FortiSwitchManager. Identified as CVE-2025-25249, this flaw could allow a remote, unauthenticated attacker to execute arbitrary code or commands through specially crafted requests. Another high-severity vulnerability affects FortiSIEM, where an OS command injection flaw (CWE-78) tracked as CVE-2025-64155 could allow unauthenticated attackers to execute unauthorized commands via crafted TCP requests. Lower-severity vulnerabilities were also documented. These include a path traversal vulnerability in FortiVoice (CVE-2025-58693), an SQL injection flaw in FortiClientEMS (CVE-2025-59922), an SSRF vulnerability in FortiSandbox (CVE-2025-67685), and an information disclosure issue in the FortiFone web portal (CVE-2025-47855). Affected Versions, Risk Ratings, and Mitigation Guidance The advisory lists a wide range of affected versions. FortiVoice versions 7.2.0 through 7.2.2 and 7.0.0 through 7.0.7 are impacted, while FortiSandbox versions 5.0.0 through 5.0.4 and all versions of 4.4, 4.2, and 4.0 are also affected. FortiOS versions from 6.4.0 through 7.6.3 are included, alongside multiple releases of FortiClientEMS, FortiSwitchManager, FortiSIEM, FortiFone, and FortiSASE. MS-ISAC assesses the risk as high for large and medium government organizations and businesses, medium for small government entities and small businesses, and low for home users. At the time of issuance, there were no reports of active exploitation in the wild. To reduce risk, MS-ISAC recommends applying Fortinet’s stable channel updates as soon as possible following appropriate testing. Additional guidance includes maintaining a formal vulnerability management and remediation process, conducting regular automated patching and vulnerability scans, and performing periodic penetration testing. Organizations are also advised to enforce least-privilege access, manage default and administrative accounts carefully, enable anti-exploitation protections, and segment networks to limit potential lateral movement.

Nicole Ozer Joins CPPA to Drive Privacy and Digital Security Initiatives
The California Privacy Protection Agency (CalPrivacy) has announced a significant leadership appointment, as Assembly Speaker Robert Rivas named Nicole Ozer to the CPPA Board, emphasising California’s ongoing commitment to strengthening consumer privacy protections. The Nicole Ozer appointment comes at a time when privacy regulation, digital rights, and responsible data governance are taking on increased importance across both state and federal institutions. Ozer brings decades of experience working at the intersection of privacy rights, technology, and democratic governance. She currently serves as the inaugural Executive Director of the Center for Constitutional Democracy at UC Law San Francisco, where her work focuses on safeguarding civil liberties in the digital age. Nicole Ozer Appointment Strengthens CalPrivacy Board Jennifer Urban, Chair of the California Privacy Protection Agency Board, welcomed the Nicole Ozer appointment, citing Ozer’s extensive background in privacy law, surveillance policy, artificial intelligence, and digital speech. “Nicole has a long history of service to Californians and deep legal and policy expertise,” Urban said. “Her knowledge will be a valuable asset to the agency as we continue advancing privacy protections across the state.” Urban also acknowledged the contributions of outgoing board member Dr. Brandie Nonnecke, noting her role in supporting CalPrivacy’s rulemaking, enforcement efforts, and public outreach initiatives over the past year. The CPPA Board plays a central role in guiding how California’s privacy laws are implemented and enforced, making leadership appointments especially critical as regulatory expectations evolve. Nicole Ozer’s Background in Privacy and Civil Liberties Before joining UC Law San Francisco, Nicole Ozer served as the founding Director of the Technology and Civil Liberties Program at the ACLU of Northern California. Her career also includes roles as a Technology and Human Rights Fellow at the Harvard Kennedy School, a Visiting Researcher at the Berkeley Center for Law and Technology, and a Fellow at Stanford’s Digital Civil Society Lab. Her work has been widely recognized, including a California Senate Members Resolution honoring her dedication to defending civil liberties in the digital world and her contributions to protecting the rights of people across California. “I appreciate the opportunity to serve on the CPPA Board,” Ozer said. “This is a critical moment to ensure that California’s robust privacy rights are meaningful in practice. I look forward to supporting the agency’s important work.” Role of the California Privacy Protection Agency The California Privacy Protection Agency is governed by a five-member board, with appointments made by the Governor, the Senate Rules Committee, the Assembly Speaker, and the Attorney General. The agency is responsible for administering and enforcing key privacy laws, including the California Consumer Privacy Act, the Delete Act, and the Opt Me Out Act. Beyond enforcement, CalPrivacy focuses on educating consumers and businesses about their rights and obligations. Through its website, Privacy.ca.gov, Californians can access guidance on protecting personal data, submitting delete requests, and using the Delete Request and Opt-out Platform (DROP). Leadership Shifts Across Security and Privacy Institutions Ozer’s appointment to the California Privacy Protection Agency Board comes in the same week as another notable leadership development at the federal level. The National Security Agency (NSA) announced the appointment of Timothy Kosiba as its 21st Deputy Director, highlighting parallel leadership changes shaping the future of privacy, cybersecurity, and national security. As NSA Deputy Director, Kosiba becomes the agency’s senior civilian leader, responsible for strategy execution, policy development, and operational oversight. His appointment was designated by Secretary of War Pete Hegseth and Director of National Intelligence Tulsi Gabbard, and formally approved by President Donald J. Trump. While the missions of the National Security Agency and the California Privacy Protection Agency differ, both appointments underline a growing emphasis on experienced leadership in institutions responsible for protecting sensitive data, infrastructure, and public trust. Together, these developments reflect how governance around privacy, cybersecurity, and digital rights continues to evolve, with leadership playing a central role in shaping how protections are implemented in practice.

PLUGGYAPE Malware Uses Signal and WhatsApp to Target Ukrainian Defense Forces
The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed details of new cyber attacks targeting its defense forces with malware known as PLUGGYAPE between October and December 2025. The activity has been attributed with medium confidence to a Russian hacking group tracked as Void Blizzard (aka Laundry Bear or UAC-0190). The threat actor is believed to be active since at least
